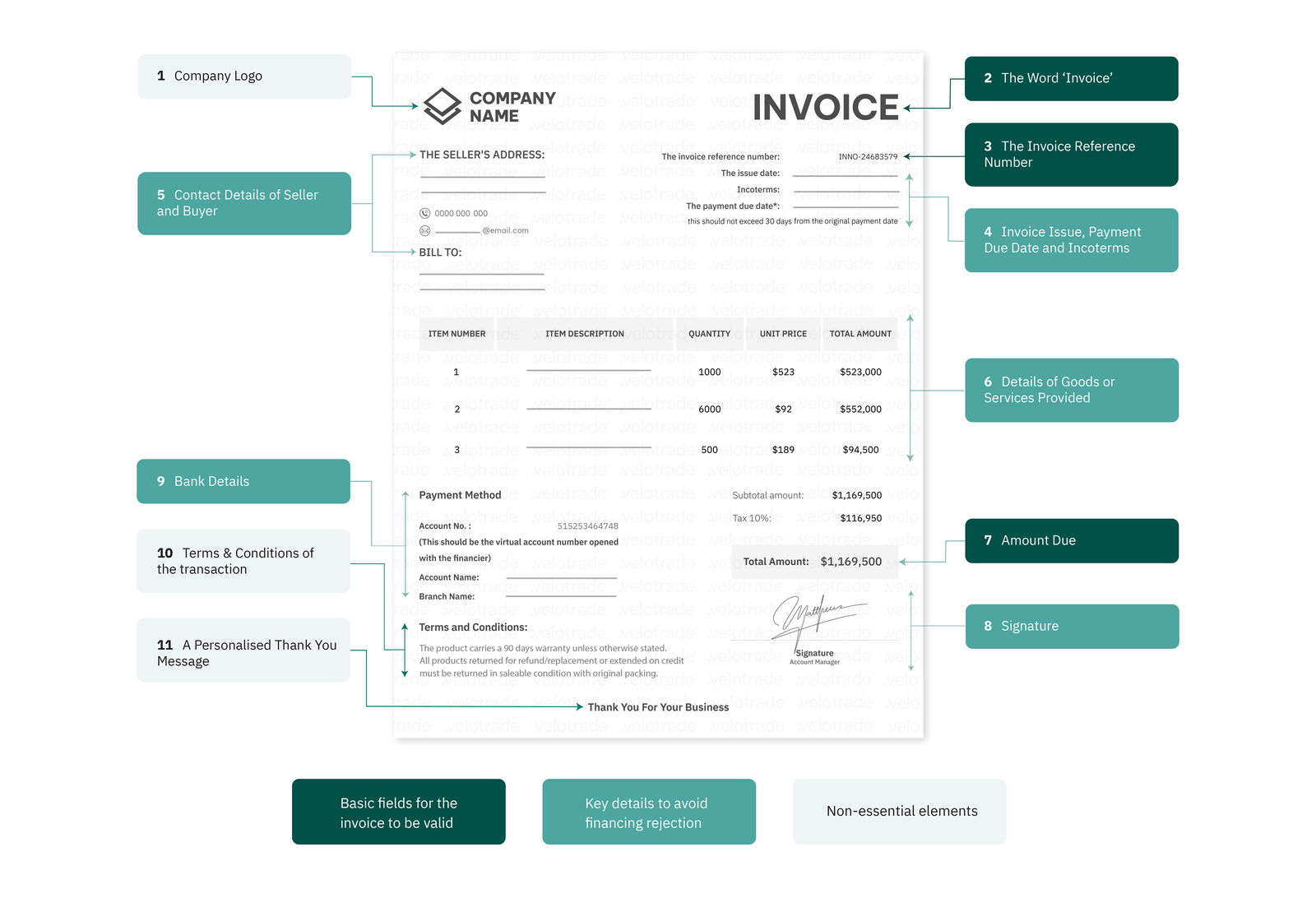
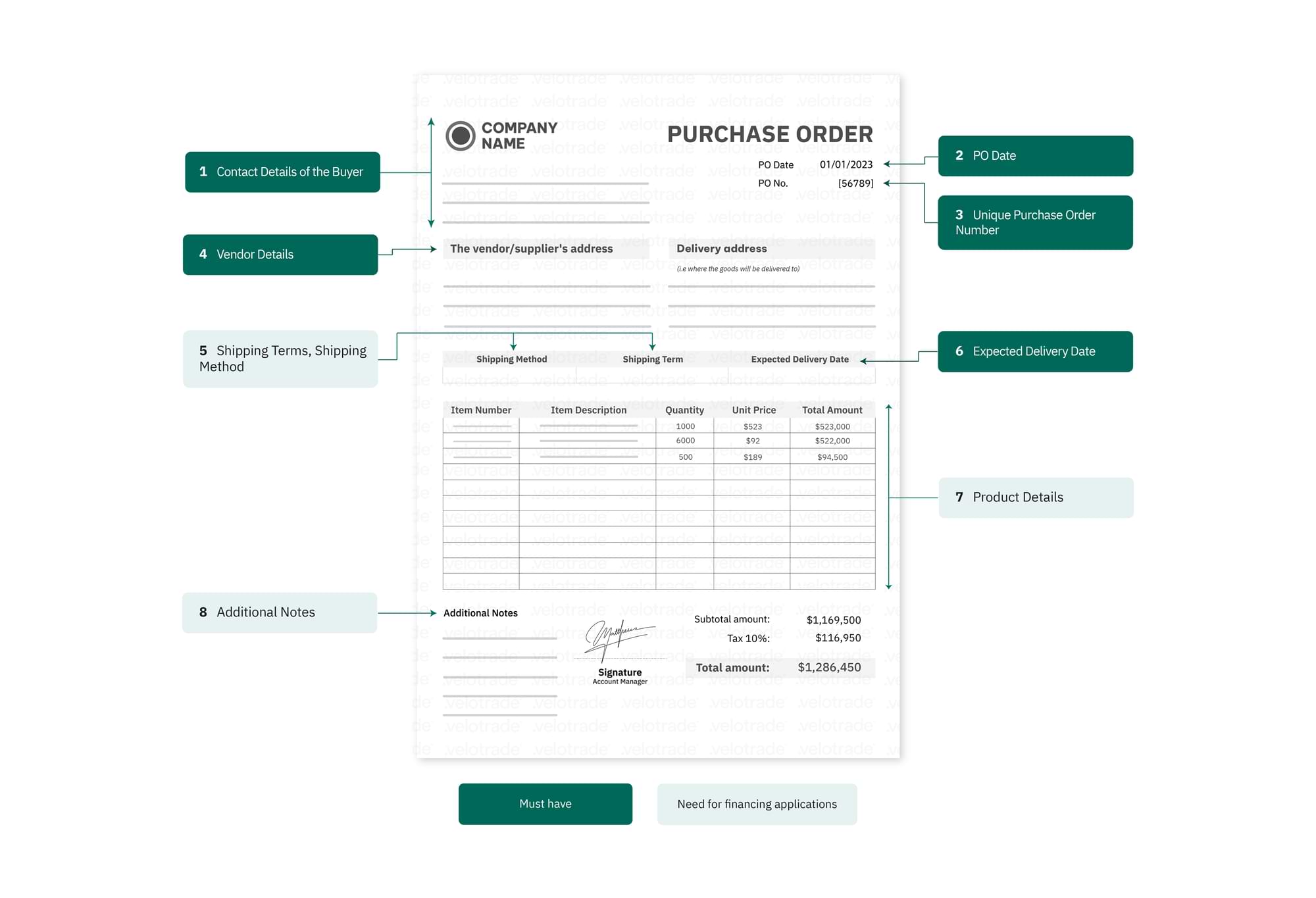
The recent SolarWinds security breach highlights the growing threat of unauthorised data access in our interconnected world.
This cyberattack went undetected for months and spread to thousands of clients. Hackers were able to spy on Fortune 500 companies such as Microsoft, Intel, Cisco and Deloitte.
They also found their way to the US government departments, including Homeland Security, Treasury and the National Nuclear Security Administration.
The engineers created backdoors and installed malicious code into SolarWinds Orion system. When the company sent out updates, it unknowingly included the hack. Each customer’s IT system was monitored, and additional malware was installed to facilitate spying.
Strong In-House Technology Team
The scale and seriousness of this breach are unprecedented, leading to a complete change in network security management.
According to IBM: A data breach can have far-reaching consequences, causing financial losses and affecting an organisation’s operations and compliance in the short term.
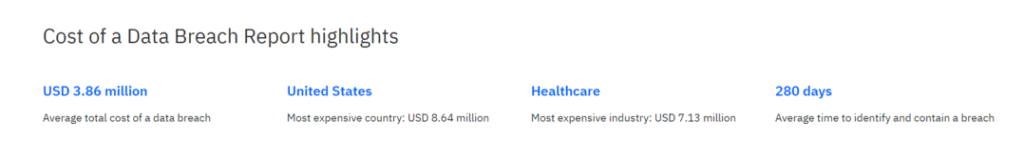
When researching your data security options, consider relevant risk factors closely.
You should look for a partner with a solid technology team and a commitment to maintain industry standards.
Our in-house Dev team scripts Velotrade’s infrastructure technology. We continuously manage software updates so that our clients are fully protected against data breaches.
For example, we use industry-leading technology to ensure the integrity of the platform:
- The code is written in JavaScript and developed using Angular software
- Kubernetes for automation and application deployment
- Amazon Web Services (AWS) acts as the primary host
Pros and Cons of Third-Party APIs

Companies in all industries can now implement applications from third-party service providers. B2C and B2B service providers are upgrading to a broader range of services.
APIs (Application Programme Interfaces) offer opportunities and threats of universal online connectivity.
- API connectivity speeds up the development of an effective online presence.
- Increases the exposure to risks linked to automation.
- APIs make it easier for hackers to find an access point to any computer system.
The SolarWinds hack points to an everyday issue faced by organisations of all types.
What is more, if much of your customer interaction takes place online – the risks can be critical to the survival of your business.
API Management
Organisations are reliant on 3rd-Party service providers as they adopt new technologies.
For this reason, 3rd-Party APIs must be carefully managed to avoid significant risks. Such risks could be:
- loss or theft of personal data
- data protection violations
- issues with money laundering and terrorist financing, especially for banks
These risks are compounded by the recent increase in remote working.
Remote working increases the likelihood of staff accessing to company servers from insecure connections.
Other dangers include:
- the widespread growth in phishing attacks
- the persistent nature of human frailty: it just takes a click to infect an entire network.
Brought to you by Velotrade, a marketplace for corporates to access financing.
Online firms are also assured of safe and reliable transactions when accessing funds with API integration in Ecommerce Financing process.
How To Mitigate Data Risks?

You can start with an effective 3rd-Party Risk Management Programme. List the inventory of each supplier’s technologies and an assessment of their risks.
The next step is harder: getting each supplier to toe the line.
For financial institutions, full compliance with GDPR or PSD2 regulations may be a sufficient incentive.
However, a great deal of careful checking is still required to ensure that all APIs meet strict requirements.
At a minimum, you will be aiming to:
- Block injection of untrusted data via APIs
- Avoid sensitive data exposure. Clouds and applications help protect all customer’s data (customer identity, credit card, et al..)
- Update the authorised access database
- Regularly update your system to protect from known risks that may undermine application defenses
- Eliminate any opportunities to execute unintended commands or access data without proper authorisation
More advanced:
- Ensure correct authentication and session management.
- Avoid security misconfiguration. All operating systems and applications must be securely configured and updated in a timely fashion.
- Ensure comprehensive logging, monitoring and report tracking.
- Avoid compromised passwords
- Check all systems for known vulnerabilities
- Correct broken access. It prevents hackers to access user accounts and modify data or admin rights.
The Future of APIs
There is no alternative to a careful, controlled system security.
Today, online businesses aim to be FinTech players in their own right. It translates into managing online transactions and handling customer funds.
However, this new level of risk and responsibility is spread across almost every sector. These online businesses could quickly become the target for bad actors to try and defraud.
In fact, the growing level of uncertainty about potential loopholes in under-managed systems can ruin an organisation of any size.
SolarWinds hack illustrates how the risk of cyber-attacks is becoming more worrying. Choosing a tech-focused financial partner is more important than ever.
Financing with Velotrade
Collateral-Free Hassle-Free Paper-Free Stress-Free
Receive payments before invoice due dates efficiently with Velotrade's financing solutions. Explore Velotrade financing solutions